Cyber Security
Cyber Security
Today, forward-thinking enterprises are already digital to the core and those that aren’t in the race will soon be in the same.
Advancements in technology such as the cloud, mobile, virtual reality (VR), blockchain, machine learning, data science, quantum computing and more will continue to reshape the way we work and live. But this involves huge risk factors. The other major change that technology has brought us is the constant threat of damage from cyber crime. Without paying the right level of attention to cyber security, digital agility can expose more interfaces to these threats.
Cyber security is the process of protecting and recovering networks, devices and programs from any type of cyber attack, cyber crimes and malicious attacks. A powerful cyber security system has numerous layers of protection spread across computers, devices, networks and programs.
As the Information technology should be protected from theft of assets, identity theft, loss of privacy and confidentiality of personal information, malicious mischief, business process, and the general activity of cybercriminals. The general public should be protected against acts of these attacks.
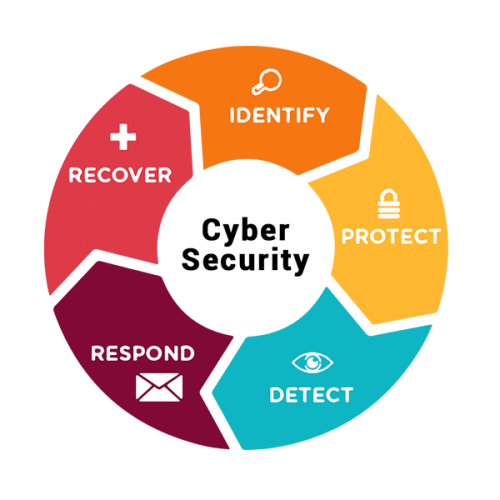
Cyber Security offer the below services :
- No data loss or competitive edge over your competition.
- It enhances overall security mechanisms of the business with the use of an improved information framework and results in smooth business management activities.
- Enhanced stakeholder support in the effective security mechanisms applied in the business.
- Understanding budget and financial resources to structure your strategy, identify priorities and finalize scope
- With the incorporation of effective cyber security mechanisms, the stolen data could be easily restored
- It identifies the vulnerabilities and weak entities that can aid an attacker to attack the system or the server. These vulnerabilities upon identification can help the teams to secure the systems in order to prevent such attacks from happening
SMKSoft cybersecurity offerings are designed to help clients plan, build and run successful cybersecurity programs. Our methodology provides actionable steps to secure systems more efficiently and provide recommendations to improve compliance with a wide variety of regulatory frameworks
Our Offerings
Offerings of Cyber Security

Virtual CISO / VISO
Virtual Chief Information Security Officer is designed for organizations that need someone to take responsibility for the growth of the information security program but don’t need a full-time.

Cyber Security
Cyber security systems and principles are designed to safeguard company data, websites and web applications from attackers seeking to disrupt, delay, alter or redirect the flow of data with the help of the Experts
Incident Response
Incident response processes help an organization respond to and manage a cyber attack. It can stop the consequences such as wreak havoc potentially affecting customers, intellectual property company time and resources

Risk Assessment
Risk assessment processes help an organization to identify, estimate, and prioritize the various risks faced by organizations, during cyber attacks
Network Security
Network security process and implementation help an Organization to prevent malicious use or accidental damage to the network’s private data, its users, or their devices. It ensures a safe network running for all legitimate users.

Managed Security Services
Managed Security Services are designed in a flexible manner to manage your compliance and security initiatives efficiently, Current IT Demands and fighting new threat adversaries